Why cross-chain bridges even exist
Most people meet bridges the hard way: you buy a token on one chain, then realize the DeFi app you want lives on another. That’s exactly why cross-chain bridge crypto infrastructure exploded from under $5B monthly volume in 2021 to peaks above $30B/month in late 2024, according to multiple analytics dashboards like DeFiLlama and Dune. A bridge is basically middleware that lets you move value or data from blockchain A to blockchain B without a central custodian holding your keys. The twist: your coins don’t literally “travel”. What actually moves is a proof that something happened on the source chain, which code on the destination chain trusts enough to mint or unlock the corresponding assets. Everything else in this article is just variations on who produces that proof and how much you trust them.
Simply put, a bridge solves the “I’m stuck on the wrong chain” problem.
Key terms in plain language
Before we trace your assets’ journey, let’s pin down some terms that docs often blur. A *source chain* is where your original tokens live before bridging (say, Ethereum). A *destination chain* is where you want usable liquidity (for example, Arbitrum or BNB Smart Chain). *Lock and mint* means the bridge smart contract locks your coins on the source chain and mints a wrapped representation on the destination. *Burn and release* is the reverse: the wrapped tokens get burned on the destination chain and the originals are unlocked on the source. A *relayer* is the entity (a script, validator set, or protocol) that observes transactions on chain A and submits a message about them to chain B. Finally, *light client* is an on-chain contract that can cryptographically verify headers from another chain without trusting any single relayer, which is crucial for a safe cross chain bridge for ethereum and bitcoin style setups.
Think of the relayer as a bilingual courier that reads one blockchain and speaks to another.
Visualizing the basic “lock and mint” bridge
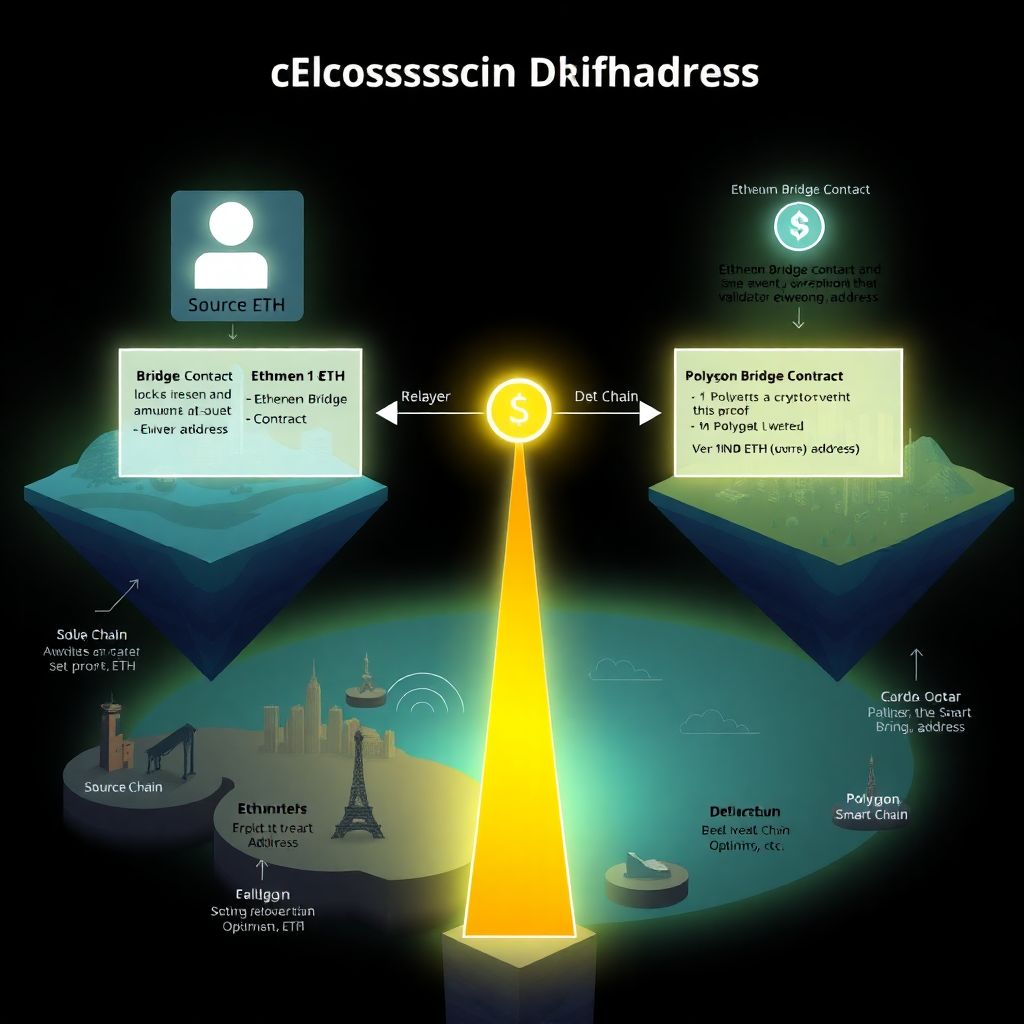
Let’s walk through a minimal example of how to transfer crypto between blockchains using a classic lock-and-mint design. Suppose you bridge 1 ETH from Ethereum to Polygon. On Ethereum, you call the bridge contract, sending 1 ETH. The contract locks it and emits an event saying “User X locked 1 ETH for Polygon, destination address Y.” Off-chain, a relayer watches Ethereum, sees this event, and later submits a transaction to the Polygon bridge contract with proof that your lock really happened. If Polygon’s bridge contract accepts the proof, it mints 1 wrapped ETH (wETH) to your address on Polygon. From your wallet’s perspective, it looks like ETH moved; under the hood, the original sits frozen, and your Polygon wETH is only as safe as that bridge’s ability to keep the locked funds and the minting logic honest and in sync.
In diagram form, your transaction looks like this:
[You] → [Ethereum Bridge: lock 1 ETH] → (Relayer passes proof) → [Polygon Bridge: mint 1 wETH].
Diagram: text-only sketch of the flow
Here’s a simple ASCII-style view of that journey:
User wallet
│ 1) send 1 ETH
▼
[Ethereum Bridge Contract]
├─ locks 1 ETH
└─ emits event: {user, amount, target_chain, target_address}
│
│ 2) relayer reads event
▼
(Relayer / Validator set)
│ 3) submits proof to Polygon
▼
[Polygon Bridge Contract]
├─ verifies proof
└─ mints 1 wETH to your Polygon address
That’s the mental picture you should keep as we compare types of cross chain bridge crypto architectures and why some are faster or cheaper but more fragile than others.
It’s really just “lock here, mint there, reverse later.”
Trusted, federated, and trustless bridges: who do you believe?
Bridge design is mostly about choosing who (or what) you trust to say, “Yes, this deposit on chain A really happened.” *Trusted bridges* rely on a single company or multisig to hold the funds and run the relayers; they’re simple and often feel like a centralized exchange withdrawal, but you’re fully exposed if that operator misbehaves. *Federated bridges* replace a single operator with a fixed validator set (e.g., 10–30 entities) that collectively sign messages; it’s better, but you still rely on an off-chain group that could collude or be hacked. *Trustless or light-client bridges* aim to minimize human trust completely. They embed a verifier for another blockchain’s consensus inside a smart contract, so any relayer can submit block headers and Merkle proofs, and the contract itself checks whether a deposit really belongs to a valid block. That’s heavier and more expensive, yet dramatically improves security for big pools of locked assets.
In practical terms, you’re always asking: “Do I trust humans here, or cryptography and consensus?”
Step-by-step: your assets’ journey through a typical bridge
Let’s narrate what you see in the wallet UI, and what’s hiding underneath. Step 1: you pick the token and networks (say USDC, from Ethereum to Arbitrum) and connect your wallet. Step 2: the UI calculates fees and estimated arrival time, often showing on-chain gas plus a bridge fee. Step 3: when you confirm, your wallet sends a transaction to the source-chain bridge contract. Step 4: once that’s confirmed (on Ethereum, ~12 seconds average), a relayer or validator cluster notices it and prepares a message for the destination chain. Step 5: on Arbitrum, a transaction submits that proof to the bridge contract, which verifies it and mints your bridged USDC. Step 6: your wallet detects the new token balance via RPC. From your point of view, you were simply using the best cross chain bridge for defi to “move” stablecoins, but what actually happened was a two-transaction protocol across two entirely separate consensus systems.
To you it feels like one smooth action, but it’s really a choreographed two-step.
How different bridge models compare to other options
Bridges are not the only way to hop ecosystems. You can also withdraw from a centralized exchange (CEX) on another chain, use a rollup’s native bridge, or trade via a DEX aggregator that abstracts bridging plus swapping. Compared to a CEX, a dedicated bridge lets you stay self-custodial and usually offers more chains and tokens, but you lose the convenience of fiat ramps and KYC-based account recovery. Versus a rollup’s canonical bridge (like the official Ethereum↔Arbitrum bridge), third-party bridges may be faster and feel like a cheap cross chain bridge with low fees thanks to liquidity pools, but they introduce additional smart-contract and liquidity risks. Versus pure DEX swaps on one chain, cross-chain swaps mix bridging with trading under the hood, adding more moving parts but saving clicks. The right choice really depends on whether you prioritize speed, cost, or minimizing trust assumptions for specific amounts.
Sometimes “withdraw from an exchange on the target chain” is still the simplest option for small sums.
Liquidity-pool bridges: swap instead of waiting
Not all bridges rely purely on lock-and-mint. Liquidity-pool bridges maintain token reserves on multiple chains. When you “bridge” 1,000 USDC from Ethereum to Optimism, you might actually just be swapping your Ethereum-side USDC into a pool, while another portion of the pool on Optimism pays you out immediately. In accounting terms, the protocol tracks IOUs between chains, and rebalances over time. This design can make the user experience feel like magic: near-instant arrival, predictable fees, and no waiting for slow finality or challenge periods. However, it shifts risk: instead of one big global vault, you now rely on the solvency and risk management of pools across multiple networks. In 2023–2024, this model grew quickly, handling a significant share of the >$20B average monthly bridge volume seen across top ecosystems.
The tradeoff is clear: faster UX in exchange for more complex liquidity management.
Security track record: why bridges get hacked so often
Bridges have been the single worst category for DeFi exploits. From 2022 through Q3 2024, public incident databases attribute over $3.5–4B in losses specifically to bridge hacks and misconfigurations, including high-profile cases like Ronin, Wormhole, Nomad, and others. The pattern is consistent: bridges centralize enormous honeypots of locked assets, but their codebases are relatively complex (multi-chain message passing, cryptography, signature aggregation). Even a tiny bug in how proofs or signatures are verified can let an attacker mint unlimited wrapped tokens or drain the vault. Statistically, while bridges represent a minority of deployed contracts, they have consistently accounted for more than 40% of total DeFi value hacked annually since 2022. As volumes grew—daily cross-chain transfer volume often exceeded $1B by late 2024—the incentive to attack these systems only increased, which is why security-conscious users care deeply about design choices and audits, not just fees.
Big TVL plus complicated logic equals prime target.
What “safe” looks like in practice
No bridge is perfectly safe, but some design traits clearly help. A safer pattern uses on-chain light clients where possible, independent audits, formal verification of critical components, and open-source repos with active maintenance. For assets like BTC or ETH moving into DeFi ecosystems, a safe cross chain bridge for ethereum and bitcoin typically avoids opaque multisigs and instead uses transparent validator sets, strict withdrawal limits, and real-time monitoring with automatic circuit breakers. Since 2022, the trend has been away from unverified bespoke code toward standardized message layers (e.g., IBC in the Cosmos world, or rollup-native bridges on Ethereum). Analytics from platforms like L2Beat and DeFiLlama show that by mid-2024, over half of the top-10 bridges by TVL had at least two independent audits and public bug bounty programs—still not perfect, but better than the 2021–2022 era when many nine-figure bridges shipped with minimal review.
So when someone says “safe bridge”, you should immediately ask: “Safe compared to what, and by whose security model?”
Fees, speed, and what “cheap” really means
Users obsess over gas costs, but bridge fees have more moving parts than a simple swap. Typical fee components include gas on both source and destination chains, a relayer fee, and sometimes a liquidity or service fee expressed as a percentage of the bridged amount. For example, moving $50 from Ethereum mainnet during peak congestion can easily burn $5–10 just in gas, even if the protocol fee is tiny; bridging the same amount from a rollup might cost under $1 all-in. When people look for a cheap cross chain bridge with low fees, they’re usually combining two desires: low protocol markup and operation on low-fee chains. From 2022 to 2024, aggregate bridging costs trended downward as L2s took more share: average per-bridge gas cost for small transfers on rollups dropped into the sub-$1 range, while user surveys show that cost sensitivity remains the main reason small holders avoid mainnet-based bridges altogether.
Cheap often means “avoid expensive base layers when possible.”
So which bridges are “best” for DeFi?
There’s no universal winner for the best cross chain bridge for defi; it depends on the pair of chains, token type, amount, and your tolerance for smart-contract and governance risk. For blue-chip paths like Ethereum ↔ major L2s, native or canonical bridges tend to be the most robust, albeit slower and sometimes costlier. For jumping between non-EVM chains and EVM DeFi, users often rely on well-established third-party protocols that have survived multiple audit cycles and supported billions in cumulative volume without critical failures. Since 2023, analytics consistently show that a handful of battle-tested bridges keep over 70% of total TVL, while dozens of smaller ones compete on UX tweaks and incentives. If you’re bridging four or five figures, it’s usually worth favoring conservative, heavily scrutinized protocols over shaving a few cents off in fees. For tiny test amounts, experimentation with newer options is more reasonable.
In short: security and reliability first, speed and coupons second—especially for serious capital.
How to pick and use a bridge safely

When you’re about to bridge funds, treat it like choosing a financial venue, not just clicking the first link in a search result. Step one: verify you’re on the official site or integrated interface of a reputable wallet or DEX aggregator; fake bridge front-ends remain a common phishing vector. Step two: check recent volumes, TVL, and audits; a protocol moving tens or hundreds of millions daily with public security reports is generally less risky than a brand-new clone with minimal liquidity. Step three: start with a small test transfer to confirm that your wallet, RPC, and token display all behave as expected on the destination chain. Also, keep an eye on community channels—if anything goes wrong with a major bridge, social feeds tend to light up quickly. Given the 2022–2024 history of multi-hundred-million-dollar exploits, a bit of paranoia is healthy whenever you push “Bridge.”
If you treat a bridge interaction like a high-value bank transfer, you’re thinking about it at the right level of seriousness.