Why cross-chain safety suddenly really matters in 2025
Cross‑chain used to be a niche thing, but by 2025 almost every serious DeFi user touches at least one bridge a week: moving stablecoins to chase yield, sending NFTs to L2s, or funding wallets on new ecosystems. That convenience comes with a price: bridges are still among the biggest honeypots in crypto, and a single bug can wipe out hundreds of millions in minutes. At the same time, UX has become so smooth that people often forget they’re using complex, experimental infrastructure. This guide is about slowing down just enough to apply a practical cross chain bridge security checklist every time you move funds, so you can enjoy cheap fees and fast finality without becoming exit liquidity for the next exploit headline.
Key concepts: what “bridging” actually does under the hood
When you use what looks like a secure cross chain bridge, you’re almost never “sending tokens across” in the literal sense. Instead, the bridge usually locks tokens on Chain A and mints a synthetic or wrapped version on Chain B, or relies on liquidity pools that let you swap native assets between networks. Validators, oracles or light clients watch both chains to confirm your deposit and trigger the corresponding action. In 2025 we also see more “native” bridging via canonical protocols built directly by major L1 and L2 teams, which reduces some risks but introduces others, like governance capture or smart contract centralization that many users underestimate until something breaks in production.
Text diagram: mental model of a typical bridge flow
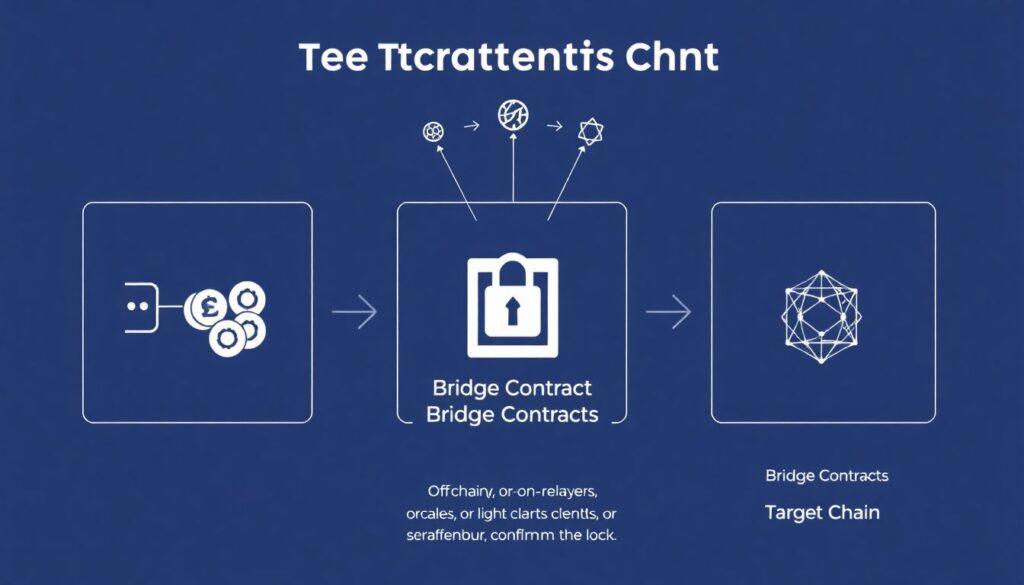
Picture it in three boxes: [User Wallet] → [Bridge Contracts] → [Target Chain]. In step one, your wallet sends USDT or ETH to a bridge contract on the source network; that’s where funds get locked. Step two, an off‑chain or on‑chain set of relayers, oracles, or light clients confirms that lock and prepares a message. Step three, on the target chain, another contract mints wrapped tokens or releases liquidity to you. In a liquidity‑based design, the diagram looks more like two pools with a messaging arrow in between. The important part: the real risk usually sits in the middle box. If that logic is flawed or the keys controlling it are compromised, your funds can be frozen or drained, even if both underlying blockchains are perfectly healthy.
Definitions you actually need before choosing a bridge
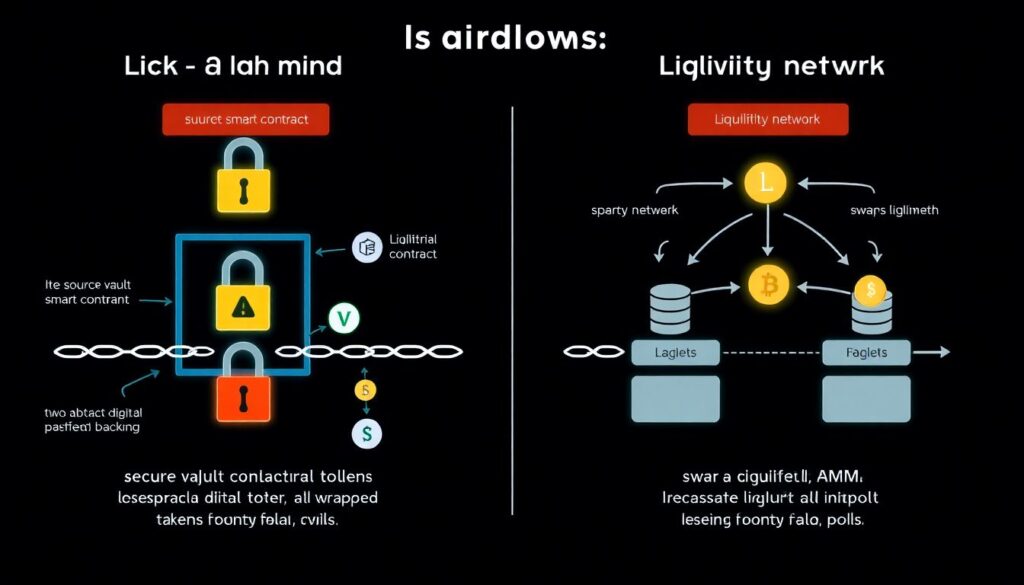
Let’s clear up a few overloaded terms. A “lock‑and‑mint” bridge holds collateral on the source chain and issues a claim token elsewhere; if that collateral contract is hacked, all wrapped assets lose backing. A “liquidity network” uses market makers or AMM pools on each side so you effectively swap assets rather than move them. A “light client bridge” verifies block headers from the other chain on‑chain, giving stronger security at the cost of more gas and complexity. Meanwhile, “canonical” often just means “endorsed by the core team,” not magically the best cross chain bridge for crypto in every scenario. Knowing which design you’re dealing with makes it easier to reason about where the actual trust assumptions and attack surfaces live.
Step 1 of the checklist: verify you’re at the real bridge
In 2025 most losses on bridges still start with something embarrassingly basic: people clicking the wrong link. Before thinking about fancy architecture, double‑check domain spelling, HTTPS certificate, and the official Twitter or Discord links from the project docs. Many phishing sites even copy the UI and simulate progress bars, but the contract addresses are different. A simple trick: in your wallet, inspect the contract you’re about to interact with and compare it to the one listed in audited documentation or reputable block explorers. If you’re learning how to safely bridge crypto between blockchains, make it a habit to bookmark trusted frontends and ignore links from random Telegram DMs, airdrop promises, or “support” accounts that answer you faster than any real team ever does.
Step 2: evaluate the protocol’s security story, not just APY
Before locking serious value anywhere, check whether the bridge has recent audits from recognizable firms, public bug bounties, and disclosed incident reports. If a project hides past exploits instead of explaining what changed, that’s a red flag. Compare that with established players: they usually document architecture decisions, have open‑source repos, and run on‑chain governance for upgrades. Also look at how keys are managed: is there a multisig, a DAO, or a hardware security module setup, and how many signatures are needed to move funds? A polished UI can make any tool look like the best cross chain bridge for crypto, but a real contender is boring in the best way: conservative configs, gradual rollouts, and clear communication about limitations instead of hyped marketing about “unhackable” technology.
Step 3: asset‑specific risks and USDT bridging nuances
Not all tokens behave the same across chains. When you look for a safe bridge to transfer USDT between chains, it matters whether you’ll receive native USDT issued by Tether on the target network or a wrapped version that only trades on a few DEXes. Native assets usually have deeper liquidity and easier redemption, while wrapped ones depend on the issuing bridge’s solvency and reputation. Also consider blacklist risk: centralized stablecoins can be frozen at the contract level if they touch sanctioned addresses, and some bridges have been caught in the crossfire after hacks. If you’re moving large treasuries or DAO funds, diversify routes and test with small amounts first, so a misconfigured path or illiquid wrapped token doesn’t trap capital where you can’t effectively use or exit it.
Step 4: simulate, size, and sanity‑check every transfer
Even with a solid secure cross chain bridge, execution mistakes can hurt. Always start with a tiny “canary” transaction to confirm the route, estimated arrival time, and final token format. Pay attention to slippage, minimum receive amounts, and any intermediate swaps, especially on aggregator frontends that auto‑route through multiple protocols. In 2025 many wallets show a step‑by‑step plan before you sign; read it like a contract, not like a cookie popup. If the gas fees, bridge fee, or final balance look off, pause. For large moves, it’s safer to split into several batches over time, reducing the blast radius if something fails mid‑migration. A calm, repeatable process beats chasing the absolute lowest fee path that shaves a few cents at the cost of doubling your cognitive load.
Comparing modern bridge types and when to use each
Today’s ecosystem mixes canonical bridges, generalized messaging protocols, and specialized liquidity layers. Canonical options are often default for simple L1↔L2 moves but may have slower withdrawals or higher gas. Messaging‑first systems are flexible but can be complex, and misconfigured apps on top of them have caused big losses. Pure liquidity bridges feel fast and user‑friendly, yet they rely heavily on external market makers. When you’re choosing how to safely bridge crypto between blockchains, match the tool to the job: for routine ETH or stablecoin moves between major rollups, stick to well‑known, battle‑tested routes; for exotic chains or new ecosystems, accept that you’re taking more experimental risk and offset it by reducing position size and avoiding time‑sensitive trades that force rushed decisions.
Ongoing habits: an always‑on cross‑chain security mindset
A one‑time cross chain bridge security checklist is good, but turning parts of it into routine is better. Keep wallets compartmentalized: one for high‑value storage, one for exploring new dApps and bridges, so approvals on experimental contracts can’t drain your main stack. Regularly revoke old allowances on both source and destination chains, especially for bridges you no longer use. Stay plugged into security channels: many incidents are spotted by on‑chain monitors and shared on social media before official announcements, giving attentive users a chance to pause new transfers. In 2025, bridging safely is less about trusting any single protocol and more about layering good practices—verification, diversification, and skepticism—so that even if one link in the chain fails, it doesn’t take your entire portfolio down with it.